Abstract:
- Over-privileged accounts create safety vulnerabilities by increasing a corporation’s assault floor
- Rockset has launched new security measures that permit admins to restrict entry to sure customers to a selected subset of information with out exposing the entire knowledge set
- RBAC with Customized Roles permits admins to create scoped down consumer roles with restricted privileges. Roles can now be assigned to API Keys so privileges by the API Key are outlined by the position
- View is a digital assortment outlined by a SQL question that permits admins to show restricted knowledge set to clients
- Rockset enhances real-time analytics with enterprise-grade safety and compliance
“The very last thing you need is to be on the entrance web page of the WSJ due to a breach.”
This quote has stayed with me ever since I began working in enterprise safety. Enterprises at present are very aware and deliberate about safety necessities with each third-party vendor they select to work with. As a result of buyer belief is all the time a core worth and high precedence, profitable enterprises are establishing belief by guaranteeing that their clients’ knowledge is all the time saved non-public and safe.
At Rockset, we serve enterprise clients from a variety of industries, and all of them inquire about our safety capabilities and the way we deal with their knowledge. Safety is high of thoughts for us identical to it’s for our clients. This manifests itself in our robust security measures and give attention to the assorted safety measures we take together with SOC 2 Sort II compliance, knowledge masking, superior encryption for knowledge in flight and at relaxation, and superior entry controls similar to native multi-factor authentication and integrations with SSO suppliers like Okta. For full information on how Rockset retains itself and its clients protected, go to the Rockset Safety Whitepaper.
A joint examine from Stanford College and safety agency Tessian revealed that 9 out of 10 knowledge breaches are attributable to workers’ errors. For that cause, offering workers with solely the naked minimal entry they should carry out their jobs is key to defending each firm knowledge and buyer knowledge. Position-Based mostly Entry Management (RBAC) is usually how corporations obtain the precept of ‘least privilege’ — offering entry to the correct folks (or providers) on the proper time, for the correct sources.
Fantastic-Tuned Management with RBAC Customized Roles
Till now, our RBAC characteristic was restricted to a handful of built-in roles for each customers and API keys they created (which inherited their position). These built-in roles had been unable to fulfill the assorted wants of our clients for full entry controls, particularly when clients used Rockset of their customer-facing purposes.
A standard use-case we hear clients ask is to restrict knowledge entry by way of a Question Lambda with an API key. Prior to now, a developer utilizing Rockset wasn’t capable of create an API key that solely allowed learn entry to a subset of information. Builders must use customized code inside their software to limit entry. This was not scalable and clients advised us they wished a extra sturdy strategy to restrict entry, each to the Rockset console and it’s API keys.
After listening to what our builders wanted, we went again to the drafting board and recognized entry privileges for each single motion on each single useful resource inside Rockset. This is able to allow us to finally construct Position-Based mostly Entry Management with Customized Roles, the characteristic we now have at present that permits our clients to create and management granular and intuitive entry controls throughout Rockset.
Here’s a pattern customized position throughout the Rockset admin console:
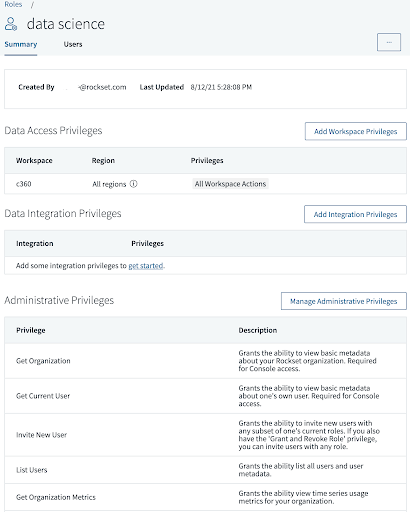
As you may see, there are three totally different sections: Knowledge Entry, Knowledge Integration, and Administrative Privileges. Every part has a special checklist of privileges that you may assign a consumer. You may additional phase knowledge entry by letting customers learn or write knowledge to solely sure Workspaces. These Workspaces are like folders, and may comprise Collections, Aliases, Question Lambdas, and Views.
Here’s a demo of Position-Based mostly Entry Management with Customized Roles:
Embedded content material: https://youtu.be/NJxshf2YQy4
Share Solely a Subset of Knowledge with Views
Did you discover {that a} customized position can now handle Views? Should you’re stunned to see Views on the above checklist of sources included in a Workspace, it’s as a result of View is one other new characteristic we’re launching! Views are saved, pre-defined SQL queries that may be queried like all different persistent knowledge in Rockset. It’s a digital, controllable have a look at knowledge that protects the underlying dataset. Views additional enhances how knowledge is accessed inside Rockset or by purposes that use Rockset as the information serving layer.
Earlier than Views, a standard safety problem for our clients was that after a Assortment was ingested into Rockset, it nonetheless may comprise delicate knowledge that some workers or clients shouldn’t have the ability to question. But, there was no strategy to expose solely a subset of information to these workers or clients. Now, with Views, you may permit these customers entry to that scoped down knowledge set with out the necessity to reingest your complete knowledge set to a different Assortment.
Moreover, if you wish to apply SQL logic earlier than the information is served to the app, now you can do that with Views, permitting your customers to right away get the solutions they’re in search of.
Right here’s what a View seems like in our console:
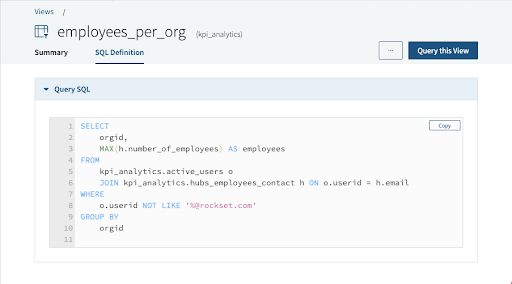
Within the examples above, the employees_per_org View could be additional queried identical to every other assortment in Rockset, together with utilizing JOINs. It can be used within the definition of a Question Lambda the identical approach that Collections are. Views usually are not solely nice for proscribing knowledge entry, however they’re additionally nice for modularizing your queries. In case you have a CTE (Widespread Desk Expression) you usually use in numerous queries, now you can substitute it with a View, and never fear about updating that CTE a number of instances throughout all these queries.
Here’s a demo of Views:
Embedded content material: https://youtu.be/CgoUJs20Vzk
Begin Utilizing Position-Based mostly Customized Roles and Views Right this moment
Managing Position-Based mostly Customized Roles and Views could be very intuitive. If you wish to apply entry controls to an software accessing Rockset by Question Lambdas or REST APIs, you merely assign the corresponding position to a given API key. Each consumer in our system can create an API key and apply the correct stage of entry privileges for that key. Customers can’t create an API key with privileges they don’t have themselves.
Along with enhancing safety, RBAC Customized Roles and Views additionally enhance software speeds by eradicating the necessity for an intermediate service layer to handle API permissions.
In abstract, RBAC Customized Roles and Views are new security measures that present highly effective entry controls for our clients. The granularity could be to any motion carried out on any useful resource on any subset of the information hosted in Rockset. With these two options mixed, our clients can apply the idea of ‘least privilege’ on Rockset and relaxation assured that their clients’ knowledge is barely accessed when, the place, and by solely the required folks and providers. Each can be found at present so give them a strive! For extra particulars on the options, please view our product paperwork for RBAC and product paperwork for Views.
