Shock! The LockBit ransomware group has re-emerged, simply days after a high-profile legislation enforcement operation seized management of its infrastructure and disrupted its operations.
“Operation Cronos” noticed international businesses all over the world work collectively to grab management of LockBit’s web site, the place data had been revealed about ransomware victims and their stolen knowledge, probably leaving many hoping that LockBit was gone for good.
Nonetheless, no less than a few of these on the coronary heart of the infamous ransomware gang have chosen to not run to the hills – however as an alternative seem to have created a brand new web site on the darkish net the place they’re itemizing what look like company victims.
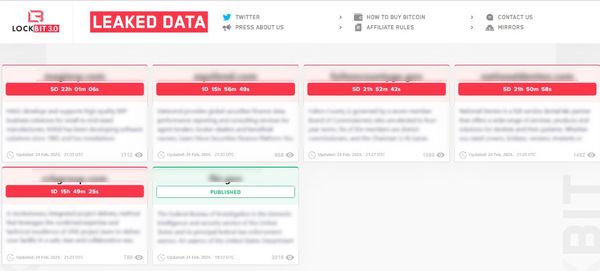
Just like the Hydra of Greek mythology, chopping off one head of LockBit would not matter – it could spawn a number of new ones. LockBit is struggling to desert a felony marketing campaign that has extorted over US $120 million.
LockBit’s secretive administrator, who makes use of the web deal with “LockBitSupp”, acknowledged that the group’s infrastructure was seemingly compromised by pc crime-fighting authorities because of their failure to patch their PHP model due to “private negligence and irresponsibility.”
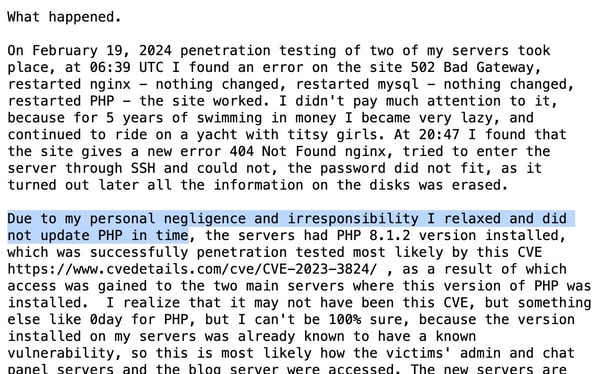
Sure, a reckless and sloppy perspective to pc safety is an issue for each firms falling sufferer to ransomware assaults and people attacking them.
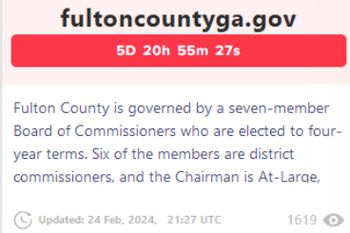
In accordance with LockBitSupp, the takedown of LockBit’s programs occurred because the group ready to launch delicate data it had stolen in a crippling assault towards authorities programs in Fulton County, Georgia.
Curiously, Fulton County restored its programs however county official Robb Pitts informed press within the hours after LockBit’s infrastructure was seized, that the county had not paid a ransom:
“This was a ransomware incident carried out by criminals for their very own monetary achieve. We couldn’t, in good conscience, use Fulton County taxpayer funds to make a cost. We didn’t pay nor did anybody pay on our behalf.”
The LockBit gang claimed that data stolen from Fulton County included paperwork associated to courtroom circumstances towards Donald Trump “that would have an effect on the upcoming US election” if leaked.
LockBitSupp went on to explain how “Personally I’ll vote for Trump.” It is unclear if that is an try to mislead observers into believing that they’re based mostly in the USA or not.
After seizing the LockBit leak website, the UK’s Nationwide Crime Company (NCA) acknowledged that it doesn’t consider LockBitSupp is predicated within the USA.
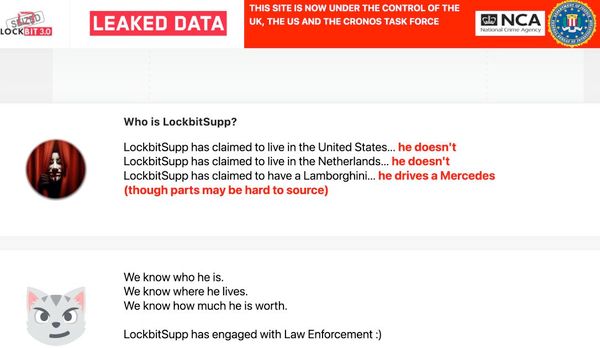
In the meantime, LockBit’s new website is threatening as soon as once more to launch knowledge beforehand stolen from Fulton County’s pc programs.
LockBitSupp’s admission about their safety failing ought to be a wake-up name for all. In case your organisation hasn’t completed an intensive safety evaluation these days, it is time. Vulnerability patching isn’t a luxurious, it’s a necessity. Safe backups and safety consciousness coaching for all workers are essential.
Rewards of as much as US $15 million are being supplied for the identification or location of key people within the LockBit gang, and the arrest and/or conviction of anybody concerned in its ransomware actions.
The struggle towards ransomware is ongoing.
