A set of faux npm packages found on the Node.js repository has been discovered to share ties with North Korean state-sponsored actors, new findings from Phylum present.
The packages are named execution-time-async, data-time-utils, login-time-utils, mongodb-connection-utils, and mongodb-execution-utils.
One of many packages in query, execution-time-async, masquerades as its reputable counterpart execution-time, a library with greater than 27,000 weekly downloads. Execution-time is a Node.js utility used to measure execution time in code.
It “really installs a number of malicious scripts together with a cryptocurrency and credential stealer,” Phylum mentioned, describing the marketing campaign as a software program provide chain assault focusing on builders. The package deal was downloaded 302 occasions since February 4, 2024, earlier than being taken down.
In an fascinating twist, the risk actors made efforts to hide the obfuscated malicious code in a take a look at file, which is designed to fetch next-stage payloads from a distant server, steal credentials from net browsers like Courageous, Google Chrome, and Opera, and retrieve a Python script, which, in flip, downloads different scripts –
- ~/.n2/pay, which may run arbitrary instructions, obtain and launch ~/.n2/bow and ~/.n2/adc, terminate Courageous and Google Chrome, and even delete itself
- ~/.n2/bow, which is a Python-based browser password stealer
- ~/.n2/adc, which installs AnyDesk on Home windows
Phylum mentioned it recognized feedback within the supply code (“/Customers/ninoacuna/”) that made it potential to trace down a now-deleted GitHub profile with the identical identify (“Nino Acuna” or binaryExDev) containing a repository known as File-Uploader.
Current throughout the repository have been Python scripts referencing the identical IP addresses (162.218.114[.]83 – subsequently modified to 45.61.169[.]99) used to fetch the aforementioned Python scripts.
It is suspected that the assault is a piece in progress, as at the very least 4 extra packages with similar options have made their method to the npm package deal repository, attracting a complete of 325 downloads –
Connections to North Korean Actors Emerge
Phylum, which additionally analyzed the 2 GitHub accounts that binaryExDev follows, uncovered one other repository often called mave-finance-org/auth-playground, which has been forked a minimum of a dozen occasions by different accounts.
Whereas forking a repository in itself is just not out of the peculiar, an uncommon facet of a few of these forked repositories have been that they have been renamed as “auth-demo” or “auth-challenge,” elevating the likelihood that the unique repository could have been shared as a part of a coding take a look at for a job interview.
The repository was later moved to banus-finance-org/auth-sandbox, Dexbanus-org/live-coding-sandbox, and mave-finance/next-assessment, indicating makes an attempt to actively get round GitHub’s takedown makes an attempt. All these accounts have been eliminated.
What’s extra, the next-assessment package deal was discovered to include a dependency “json-mock-config-server” that is not listed on the npm registry, however fairly served straight from the area npm.mave[.]finance.
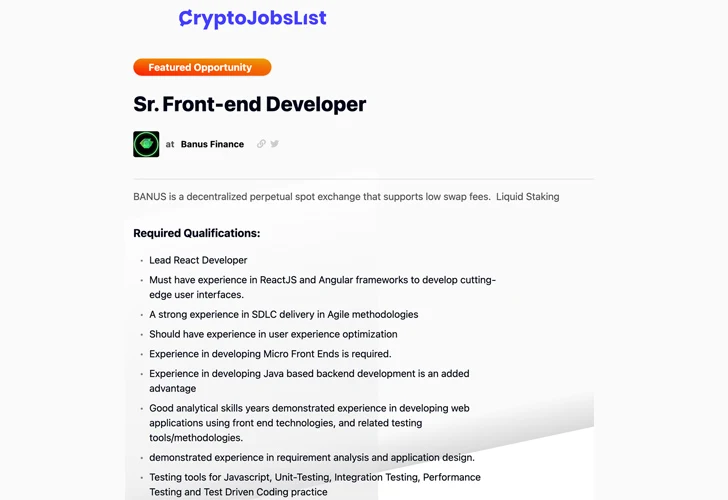
It is price noting that Banus claims to be a decentralized perpetual spot trade based mostly in Hong Kong, with the corporate even posting a job alternative for a senior frontend developer on February 21, 2024. It is at present not clear if this can be a real job opening or if it is an elaborate social engineering scheme.
The connections to North Korean risk actors come from the truth that the obfuscated JavaScript embedded within the npm package deal overlaps with one other JavaScript-based malware dubbed BeaverTail that is propagated by way of an analogous mechanism. The marketing campaign was codenamed Contagious Interview by Palo Alto Networks Unit 42 in November 2023.
Contagious Interview is slightly completely different from Operation Dream Job – which is linked to the Lazarus Group – in that it is primarily targeted on focusing on builders via faux identities in freelance job portals to trick them into putting in rogue npm packages, Michael Sikorski, vice chairman and CTO of Palo Alto Networks Unit 42, instructed The Hacker Information on the time.
One of many builders who fell sufferer to the marketing campaign has since confirmed to Phylum that the repository is shared beneath the guise of a stay coding interview, though they mentioned they by no means put in it on their system.
“Greater than ever, it will be important for each particular person builders in addition to software program growth organizations to stay vigilant in opposition to these assaults in open-source code,” the corporate mentioned.