Two new vulnerabilities affect ConnectWise ScreenConnect, distant desktop and entry software program used for help: CVE-2024-1709 and CVE-2024-1708, with the previous being significantly harmful for organizations.
The CVE-2024-1709 vulnerability, which impacts ScreenConnect 23.9.7 and prior, permits any distant attacker to bypass authentication to delete the ScreenConnect consumer database and get management of an admin consumer. Huge exploitation by attackers is ongoing within the wild, with greater than 3,000 weak situations reachable from the web. Safety corporations have noticed ransomware, info stealers and Cobalt Strike payloads, to call just a few, being put in after profitable exploitation of the vulnerability.
The CVE-2024-1708 vulnerability, which isn’t as extreme as CVE-2024-1709, permits path traversal, which allows an attacker to entry recordsdata and directories that shouldn’t be accessible.
Technical particulars concerning the ScreenConnect CVE-2024-1709 vulnerability
U.S.-based cybersecurity firm Huntress launched technical particulars concerning the ScreenConnect CVE-2024-1708 and CVE-2024-1709 vulnerabilities, the latter being significantly harmful as a result of a easy request to a particular path on uncovered situations permits an attacker to hook up with the setup wizard of the occasion (Determine A).
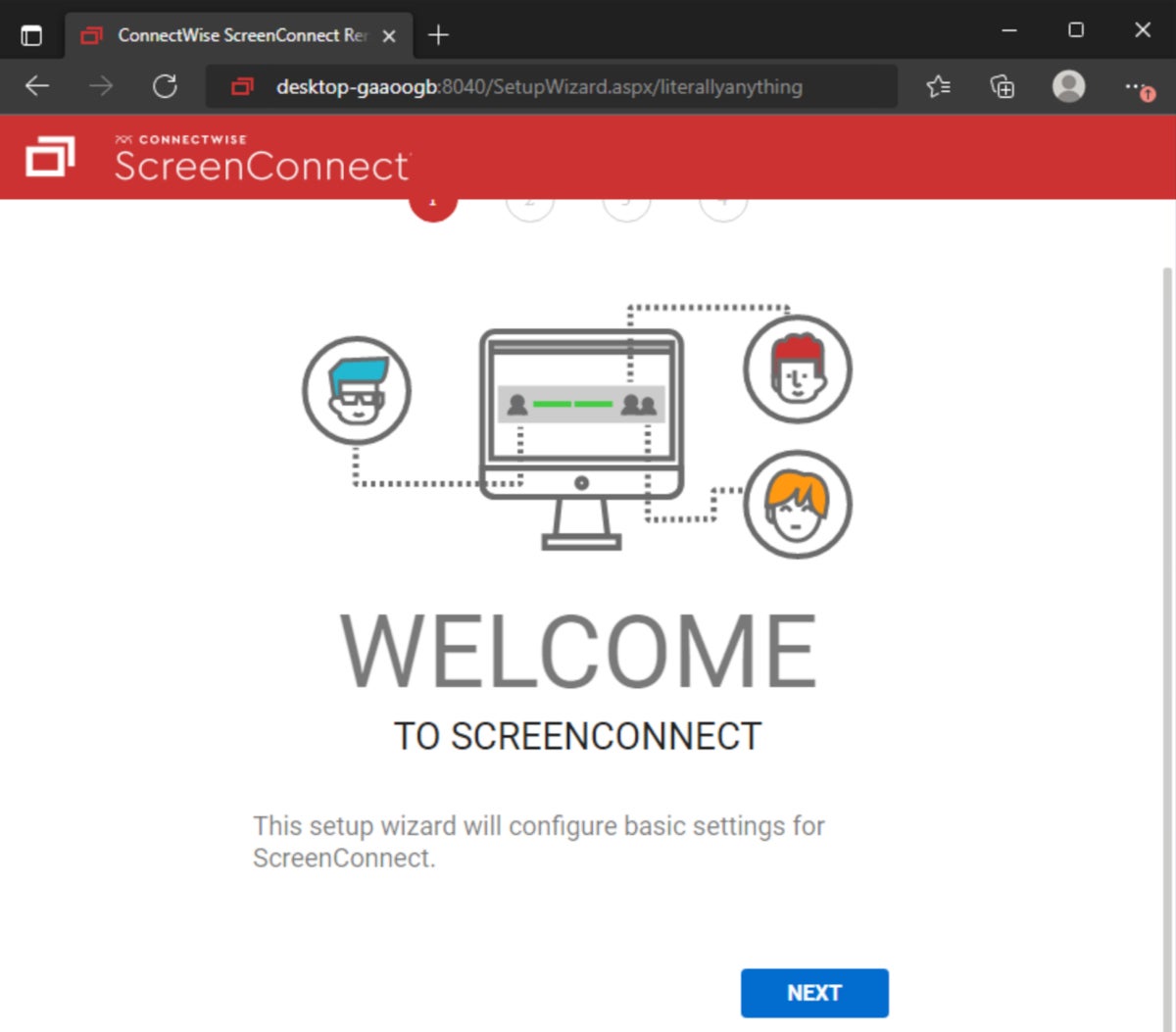
As defined by Huntress researchers, the setup wizard is chargeable for establishing the preliminary admin consumer and putting in a license on the system. The Huntress staff wrote, “The consumer creation portion of this setup occurs instantly after clicking the ‘Subsequent’ button on the setup web page, so there isn’t any want to finish the setup wizard absolutely to use the system.” If an attacker completes this step, the interior consumer database might be absolutely overwritten, and all native customers might be deleted, leaving solely the attacker as administrator of the occasion.
As soon as that is executed, it’s trivial to create and add a malicious ScreenConnect extension to achieve full distant code execution on the occasion, in response to the researchers.
One other vulnerability has additionally been reported, CVE-2024-1708, which is a less-severe vulnerability permitting path traversal.
Huge exploitation of CVE-2024-1709 within the wild has began
Proof of idea for exploiting CVE-2024-1709 has been printed on GitHub, exhibiting tips on how to add a brand new consumer to the compromised system.
Cybersecurity firm Sophos noticed a number of assaults on Feb. 21, 2024, with attackers dropping ransomware constructed with the LockBit builder device on 30 buyer networks. Essential notice: Using the LockBit ransomware builder device doesn’t imply that it has ties with the LockBit builders, particularly when the LockBit infrastructure was just lately taken down. Any cybercriminal with entry to the builder may be behind these assaults, and the ransom notice noticed by Sophos talked about the “buthtiRansom” variant. Sophos said that one other ransomware primarily based on the LockBit builder referred to as “LockBit Black” was noticed however did not deploy in a buyer atmosphere.
Password stealers, RATs and Cobalt Strike payloads
Cybersecurity assaults aside from ransomware are presently hitting the uncovered weak situations of ScreenConnect; for example, password stealers (corresponding to Vidar/Redline) or RATs (corresponding to AsyncRAT) have additionally been noticed within the wild after exploitation of the CVE-2024-1709 vulnerability.
Cobalt Strike payloads have additionally hit uncovered ScreenConnect situations. Sophos noticed three related assaults dropping a .cmd file within the momentary folder the place ScreenConnect downloads recordsdata earlier than executing it. The cmd tried to launch PowerShell to obtain an extra payload however failed resulting from endpoint safety.
Hundreds of uncovered ScreenConnect situations, totally on U.S.-based IP addresses
ONYPHE, a French cyber protection search engine devoted to assault floor discovery & assault floor administration, supplied TechRepublic with statistics about uncovered ScreenConnect situations.
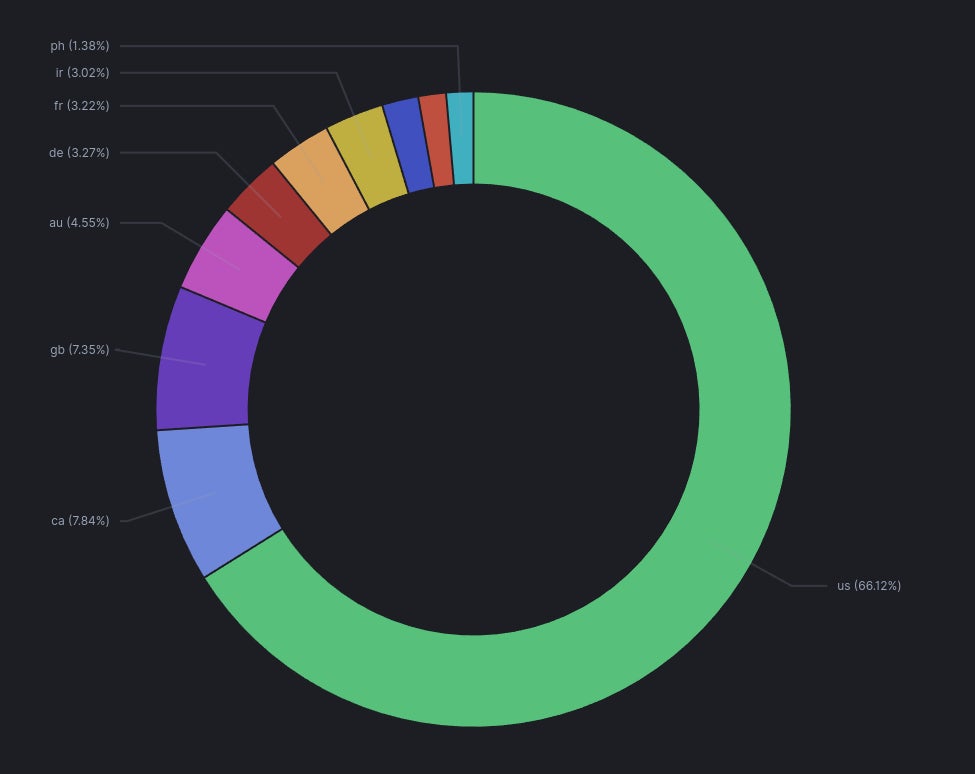
Between Feb. 19-25, 2024, ONYPHE noticed 5,731 uncovered ScreenConnect distinctive IP addresses, with 3,284 of these being weak to CVE-2024-1709. Most of these situations are operating on U.S.-based IP addresses (66.12%), adopted by Canada (7.84%) and the U.Ok. (7.35%) (Determine B).
The right way to defend from exploitation by way of these ConnectWise ScreenConnect vulnerabilities
The right way to detect exploitation of those ConnectWise ScreenConnect vulnerabilities
Concerning detection, attempting to find the sample “/SetupWizard.aspx/” in server logs may point out an assault try. The “%ProgramFiles(x86)%ScreenConnectApp_Extensions” folder must also be monitored, because it may be used for storing and executing attackers’ payloads.
The right way to defend your online business from these ConnectWise ScreenConnect exploits
ConnectWise indicated in its safety bulletin on Feb. 23, 2024 that “they’ve taken an exception step to help companions now not below upkeep by making them eligible to put in model 22.4 at no extra price, which can repair CVE-2024-1709.”
SEE: Obtain this Incident Reporting and Response Procedures Coverage from TechRepublic Premium
ConnectWise recommends on-premise companions instantly replace ScreenConnect to 23.9.8 or greater to remediate reported vulnerabilities. ConnectWise has additionally rolled out an extra mitigation step for unpatched, on-premise customers that suspends an occasion if it’s not on model 23.9.8 or later.
Cloud companions are remediated in opposition to the vulnerabilities reported by ConnectWise. On-prem companions are suggested to instantly improve to the most recent model of ScreenConnect. ConnectWise has eliminated license restrictions, so companions now not below upkeep can improve to the most recent model of ScreenConnect.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.
