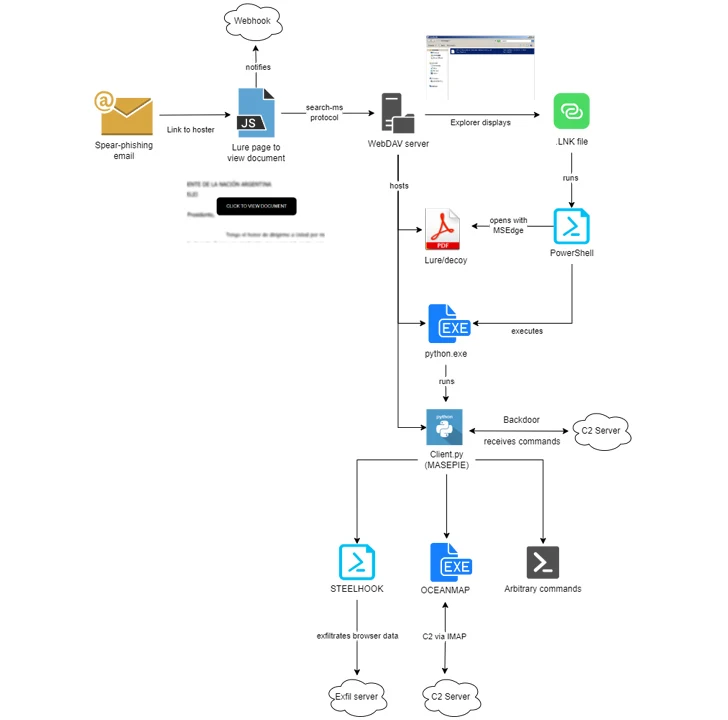
The Russia-linked risk actor often called APT28 has been linked to a number of ongoing phishing campaigns that make use of lure paperwork imitating authorities and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South America.
“The uncovered lures embody a combination of inner and publicly obtainable paperwork, in addition to attainable actor-generated paperwork related to finance, vital infrastructure, government engagements, cyber safety, maritime safety, healthcare, enterprise, and protection industrial manufacturing,” IBM X-Drive mentioned in a report revealed final week.
The tech firm is monitoring the exercise beneath the moniker ITG05, which is often known as Blue Athena, BlueDelta, Fancy Bear, Preventing Ursa, Forest Blizzard (previously Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, TA422, and UAC-028.
The disclosure comes greater than three months after the adversary was noticed utilizing decoys associated to the continuing Israel-Hamas struggle to ship a customized backdoor dubbed HeadLace.
APT28 has since additionally focused Ukrainian authorities entities and Polish organizations with phishing messages designed to deploy bespoke implants and data stealers like MASEPIE, OCEANMAP, and STEELHOOK.
Different campaigns have entailed the exploitation of safety flaws in Microsoft Outlook (CVE-2023-23397, CVSS rating: 9.8) to plunder NT LAN Supervisor (NTLM) v2 hashes, elevating the likelihood that the risk actor might leverage different weaknesses to exfiltrate NTLMv2 hashes to be used in relay assaults.
The newest campaigns noticed by IBM X-Drive between late November 2023 and February 2024 leverage the “search-ms:” URI protocol handler in Microsoft Home windows to trick victims into downloading malware hosted on actor-controlled WebDAV servers.
There may be proof to recommend that each the WebDAV servers, in addition to the MASEPIE C2 servers, could also be hosted on compromised Ubiquiti routers, a botnet comprising which was taken down by the U.S. authorities final month.
The phishing assaults impersonate entities from a number of nations comparable to Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the U.S., placing to make use of a mixture of genuine publicly obtainable authorities and non-government lure paperwork to activate the an infection chains.
“In an replace to their methodologies, ITG05 is using the freely obtainable internet hosting supplier, firstcloudit[.]com to stage payloads to allow ongoing operations,” safety researchers Joe Fasulo, Claire Zaboeva, and Golo Mühr mentioned.
The climax of APT28’s elaborate scheme ends with the execution of MASEPIE, OCEANMAP, and STEELHOOK, that are designed to exfiltrate information, run arbitrary instructions, and steal browser information. OCEANMAP has been characterised as a extra succesful model of CredoMap, one other backdoor beforehand recognized as utilized by the group.
“ITG05 stays adaptable to adjustments in alternative by delivering new an infection methodologies and leveraging commercially obtainable infrastructure, whereas persistently evolving malware capabilities,” the researchers concluded.