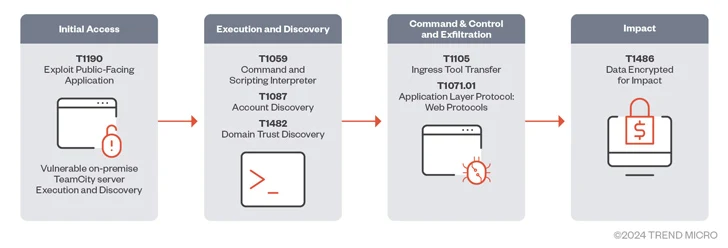
A number of menace actors are exploiting the lately disclosed safety flaws in JetBrains TeamCity software program to deploy ransomware, cryptocurrency miners, Cobalt Strike beacons, and a Golang-based distant entry trojan known as Spark RAT.
The assaults entail the exploitation of CVE-2024-27198 (CVSS rating: 9.8) that permits an adversary to bypass authentication measures and achieve administrative management over affected servers.
“The attackers are then in a position to set up malware that may attain out to its command-and-control (C&C) server and carry out further instructions resembling deploying Cobalt Strike beacons and distant entry trojans (RATs),” Development Micro mentioned in a brand new report.
“Ransomware can then be put in as a last payload to encrypt recordsdata and demand ransom funds from victims.”
Following public disclosure of the flaw earlier this month, it has been weaponized by menace actors related to BianLian and Jasmin ransomware households, in addition to to drop the XMRig cryptocurrency miner and Spark RAT.
Organizations counting on TeamCity for his or her CI/CD processes are beneficial to replace their software program as quickly as attainable to safeguard towards potential threats.
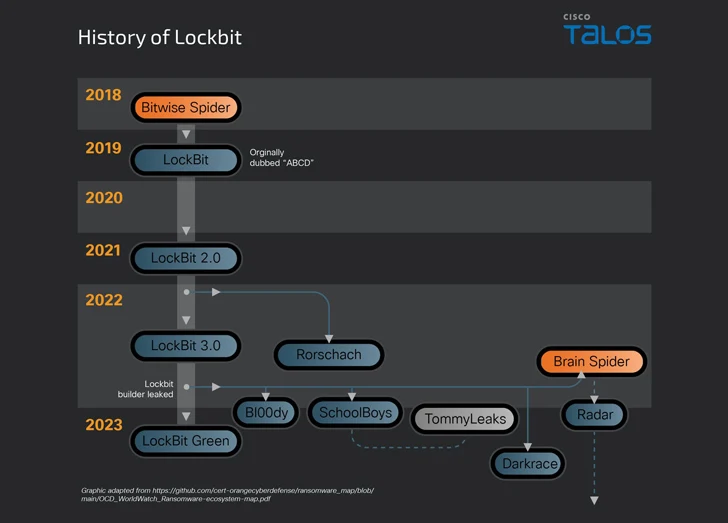
The event comes as ransomware continues to be each formidable and worthwhile, with new strains like DoNex, Evil Ant, Lighter, RA World, and WinDestroyer rising within the wild, whilst infamous cybercrime crews like LockBit are nonetheless accepting associates into their program regardless of regulation enforcement actions towards them.
WinDestroyer, specifically, stands out for its means to encrypt recordsdata and render focused programs unusable with no means to recuperate the info, elevating the chance that the menace actors behind it are geopolitically motivated.
“One of many main points when tackling ransomware crime is the character of the associates program, with actors typically working for a number of RaaS outfits at a time,” Cisco Talos mentioned. “It should take persistent, strategic efforts to considerably harm RaaS operations and weaken the regenerative energy of those gangs.”
Information shared by the U.S. Federal Bureau of Investigation’s (FBI) Web Crime Criticism Middle (IC3) reveals that 2,825 ransomware infections have been reported in 2023, inflicting adjusted losses of greater than $59.6 million. Of those, 1,193 got here from organizations belonging to a vital infrastructure sector.
The highest 5 ransomware variants impacting vital infrastructure within the U.S. embody LockBit, BlackCat (aka ALPHV or Noberus), Akira, Royal, and Black Basta.
Apart from providing an even bigger chunk of the proceeds to court docket associates, the panorama is witnessing elevated collaboration between completely different ransomware teams that share their malicious tooling with one another.
These partnerships additionally manifest within the type of ghost teams, through which one ransomware operation outsources its expertise to a different, as seen within the case of Zeon, LockBit, and Akira.
Broadcom-owned Symantec, in a report printed final week, revealed that “ransomware exercise stays on an upward development regardless of the variety of assaults claimed by ransomware actors reducing by barely greater than 20% within the fourth quarter of 2023.”
In keeping with statistics printed by NCC Group, the overall variety of ransomware instances in February 2024 elevated by 46% from January, up from 285 to 416, led by LockBit (33%), Hunters (10%), BlackCat (9%), Qilin (9%), BianLian (8%), Play (7%), and 8Base (7%).
“Current regulation enforcement exercise has the potential to polarize the ransomware panorama, creating clusters of smaller RaaS operators which might be extremely energetic and tougher to detect on account of their agility in underground boards and markets,” Matt Hull, world head of menace intelligence at NCC Group, mentioned.
“It seems that the eye drawn by the bigger ‘model’ ransomware, resembling LockBit and Cl0p, is resulting in new and small generic RaaS affiliate partnerships turning into the norm. Consequently, detection and attribution may turn into tougher, and associates might simply swap suppliers on account of low entry thresholds and minimal financial involvement.”
This has additionally been complemented by menace actors discovering novel methods to contaminate victims by primarily exploiting vulnerabilities in public-facing functions and evade detection, in addition to refining their ways by more and more banking on reputable software program and living-off-the-land (LotL) methods.
Additionally widespread amongst ransomware attackers are utilities like TrueSightKiller, GhostDriver, and Terminator, which leverage the Deliver Your Personal Weak Driver (BYOVD) method to disable safety software program.
“BYOVD assaults are engaging to menace actors, as they will present a way by which to disable AV and EDR options on the kernel stage,” Sophos researchers Andreas Klopsch and Matt Wixey mentioned in a report this month. “The sheer quantity of recognized susceptible drivers signifies that attackers have a wealth of choices to select from.”