A menace actor quietly spent the final two years integrating themself within the core crew of maintainers of XZ Utils, a free software program command-line knowledge compressor extensively utilized in Linux programs. The attacker slowly managed to combine a backdoor within the software program that was designed to intervene with SSHD and permit distant code execution by way of an SSH login certificates. The backdoor was found a couple of days earlier than being launched on a number of Linux programs worldwide.
The menace actor is suspected to be a developer with or utilizing the title Jian Tan. A number of safety specialists imagine this provide chain assault is likely to be state sponsored.
What’s XZ Utils, and what’s the XZ backdoor?
XZ Utils and its underlying library liblzma is a free software program software that implements each XZ and LZMA, that are two compression/decompression algorithms extensively utilized in Unix-based programs, together with Linux programs. XZ Utils is utilized by many operations on these programs for compressing and decompressing knowledge.
The CVE-2024-3094 backdoor present in XZ Utils was applied to intervene with authentication in SSHD, the OpenSSH server software program that handles SSH connections. The backdoor enabled an attacker to execute distant code by way of an SSH login certificates. Solely XZ Utils variations 5.6.0 and 5.6.1 are impacted.
How the XZ backdoor was applied cautiously for greater than years
On March 29, 2024, Microsoft software program engineer Andres Freund reported the invention of the backdoor. He discovered it when he grew to become keen on odd conduct of a Debian sid set up, comparable to SSH logins taking quite a lot of CPU and Valgrind errors and determined to investigate the signs in depth. Freund defined that the invention of the backdoor in XZ was luck, because it “actually required quite a lot of coincidences.”
But it seems that the implementation of the backdoor has been a really quiet course of that took about two years. In 2021, a developer named Jian Tan, username JiaT75, appeared out of the blue to start out engaged on the XZ Utils code, which isn’t uncommon as a result of builders of free software program typically work collectively on updating code. Tan contributed regularly to the XZ mission since late 2021, slowly constructing belief in the neighborhood.
In Could 2022, an unknown person utilizing the faux title Dennis Ens complained on the XZ mailing checklist that the software program replace was not satisfying. One other unknown person, Jigar Kumar, got here into the dialogue two instances to strain the principle developer of XZ Utils, Lasse Collin, so as to add a maintainer to the mission. “Progress won’t occur till there’s new maintainer,” Jigar Kumar wrote. “Why wait till 5.4.0 to vary maintainer? Why delay what your repo wants?”
In the meantime, Collin expressed that “Jia Tan has helped me off-list with XZ Utils and he may need a much bigger function sooner or later a minimum of with XZ Utils. It’s clear that my assets are too restricted (thus the numerous emails ready for replies) so one thing has to vary in the long run.” (Collin wrote Jia in his message whereas different messages reference Jian. So as to add to the confusion, Jian’s nickname is JiaT75.)
Within the months that adopted, Tan grew to become more and more concerned in XZ Utils and have become co-maintainer of the mission. In February 2024, Tan issued commits for variations 5.6.0 and 5.6.1 of XZ Utils, each of which contained the backdoor.
Additionally it is fascinating to notice that in July 2023, Tan requested to disable ifunc (GNU oblique perform) on oss-fuzz, a public software made to detect software program vulnerabilities. That operation was most likely carried out to permit the backdoor in XZ to remain undetected as soon as it was launched, because the backdoor makes use of that perform to attain its targets.
Lastly, a number of individuals chargeable for completely different Linux distributions have been contacted by the attacker to incorporate the backdoored variations of XZ Utils in their very own distributions. Richard WM Jones from RedHat wrote about it on a discussion board: “Very annoying – the obvious creator of the backdoor was in communication with me over a number of weeks making an attempt to get xz 5.6.x added to Fedora 40 & 41 due to it’s ‘nice new options’. We even labored with him to repair the valgrind challenge (which it seems now was attributable to the backdoor he had added). We needed to race final night time to repair the issue after an inadvertent break of the embargo. He has been a part of the xz mission for two years, including all kinds of binary take a look at recordsdata, and to be trustworthy with this degree of sophistication I might be suspicious of even older variations of xz till confirmed in any other case”. Tan additionally tried to have it included in Ubuntu.
XZ backdoor: A extremely technical assault
Along with the extremely elaborated social engineering lined beforehand on this article, the backdoor itself could be very complicated.
Microsoft’s senior menace researcher Thomas Roccia designed and revealed an infographic to point out the entire operation resulting in CVE-2024-3094 (Determine A).
Determine A
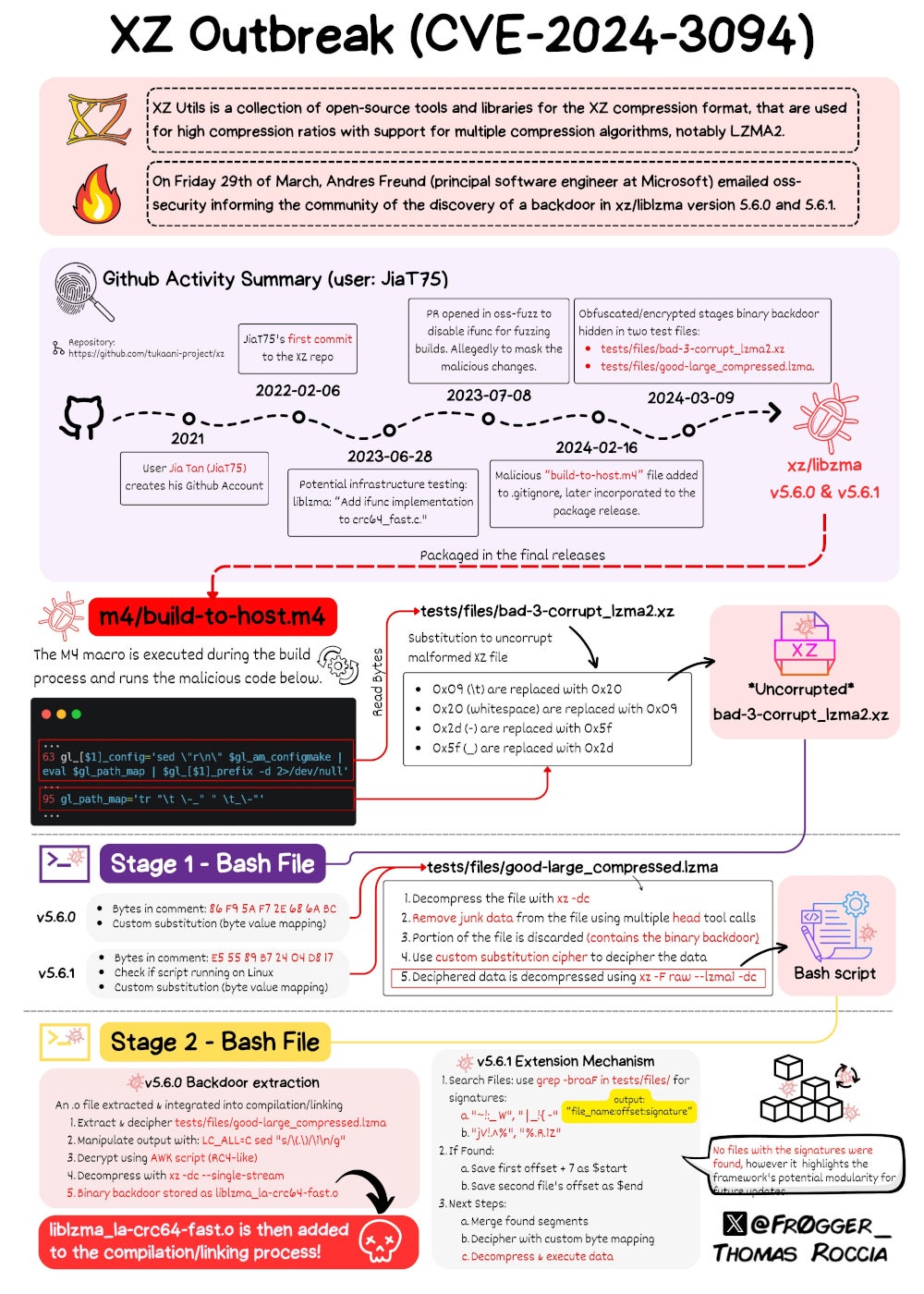
The backdoor consists of a number of components which have been included over a number of commits on the XZ Utils GitHub, described in depth by Freund.
Gynvael Coldwind, managing director of HexArcana Cybersecurity GmbH,a cybersecurity firm offering consulting and programs companies, wrote in an in depth evaluation of the backdoor that “somebody put quite a lot of effort for this to be fairly harmless trying and decently hidden. From binary take a look at recordsdata used to retailer payload, to file carving, substitution ciphers, and an RC4 variant applied in AWK all carried out with simply normal command line instruments. And all this in 3 levels of execution, and with an ‘extension’ system to future-proof issues and never have to vary the binary take a look at recordsdata once more.”
DOWNLOAD: Open supply fast glossary from TechRepublic Premium
Martin Zugec, technical options director at Bitdefender, mentioned in a press release supplied to TechRepublic that “this seems to be a meticulously deliberate, multi-year assault, probably backed by a state actor. Contemplating the huge efforts invested and the low prevalence of susceptible programs we’re seeing, the menace actors accountable have to be extraordinarily sad proper now that their new weapon was found earlier than it may very well be extensively deployed.”
Which working programs are impacted by the XZ backdoor?
Due to Freund’s discovery, the assault was stopped earlier than being unfold on a wider scale. The cybersecurity firm Tenable uncovered the next working programs recognized to be affected by the XZ backdoor:
- Fedora Rawhide.
- Fedora 40 Beta.
- Fedora 41.
- Debian testing, unstable and experimental distributions variations 5.5.1alpha-01 to five.6.1-1.
- openSUSE Tumbleweed.
- openSUSE MicroOS.
- Kali Linux.
- Arch Linux.
In a weblog put up, Crimson Hat reported that no variations of Crimson Hat Enterprise Linux are affected by CVE-2024-3094.
Debian indicated that no steady model of the distribution are affected, and Ubuntu posted that no launched variations of Ubuntu have been affected.
MacOS homebrew package deal supervisor reverted XZ from 5.6.x to five.4.6, an older but secure model. Bo Anderson, maintainer and Homebrew technical steering committee member, declared that Homebrew doesn’t “… imagine Homebrew’s builds have been compromised (the backdoor solely utilized to deb and rpm builds) however 5.6.x is being handled as not reliable and as a precaution we’re forcing downgrades to five.4.6.”
How you can mitigate and shield from this XZ backdoor menace
Extra programs is likely to be affected, particularly these on which builders compiled the susceptible variations of XZ. Safety firm Binarly gives an internet detection software that may very well be used to check programs to see if they’re affected by the XZ backdoor.
The model of XZ needs to be fastidiously checked, as variations 5.6.0 and 5.6.1 comprise the backdoor. It’s suggested to revert to a earlier recognized secure model of XZ Utils, comparable to 5.4.
Software program provide chain assaults are growing
As beforehand reported on TechRepublic, software program provide chain assaults are more and more being utilized by menace actors.
But traditional software program provide chain assaults largely encompass managing to compromise a key account within the means of the event of software program, and use the account to push malicious content material to reliable software program, which frequently will get detected fairly quickly. Within the XZ Utils case, it is extremely completely different as a result of the menace actor fastidiously managed to realize the belief of reliable builders and turn into one of many maintainers of the software, permitting him to slowly push completely different susceptible components of code into the software program with out being seen.
Software program provide chain assaults aren’t the one growing threats; different provide chain assaults based mostly on IT merchandise are additionally growing.
Subsequently, corporations ought to make sure that third events are considered of their assault floor monitoring.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.
