The content material of this submit is solely the duty of the creator. AT&T doesn’t undertake or endorse any of the views, positions, or info supplied by the creator on this article.
Within the area of digital forensics, unstable information assumes a paramount position, characterised by its ephemeral nature. Analogous to fleeting whispers in a bustling metropolis, unstable information in Linux programs resides transiently throughout the Random Entry Reminiscence (RAM), encapsulating essential system configurations, energetic community connections, operating processes, and traces of consumer actions. As soon as a Linux machine powers down, this ephemeral reservoir of data dissipates swiftly, rendering it irretrievable.
Recognizing the importance of well timed incident response and the crucial of developing an in depth timeline of occasions, this weblog embarks on an exhaustive journey, delineating a scientific method fortified with greatest practices and indispensable instruments tailor-made for the acquisition of unstable information throughout the Linux ecosystem.
Conceptually, unstable information serves as a mirror reflecting the real-time operational panorama of a system. It embodies a dynamic tapestry of insights, starting from system settings and community connectivity to program execution and consumer interactions. Nevertheless, the transient nature of this information necessitates proactive measures to seize and analyse it earlier than it evaporates into the digital void.
In pursuit of elucidating this intricate course of, we delve right into a meticulous exploration, elucidating every side with precision and readability. By a curated synthesis of established methodologies and cutting-edge instruments, we equip forensic practitioners with the requisite information and expertise to navigate the complexities of unstable information acquisition in reside Linux environments.
Be part of us as we unravel the intricacies of digital forensics, embark on a journey of discovery, and empower ourselves with the instruments and methods essential to unlock the secrets and techniques hid inside reside Linux programs.
Earlier than continuing, it is vital to know what unstable information encompasses and why it is so necessary in investigations:
System Necessities:
- Hostname: Identifies the system
- Date and Time: Contextualizes occasions
- Timezone: Helps correlate actions throughout areas
- Uptime: Reveals system state period
Community Footprint:
- Community Interfaces: Lively connections and configurations
- Open Ports: Potential entry factors and companies uncovered
- Lively Connections: Exhibits reside communication channels
Course of Ecosystem:
- Operating Processes: Lively applications and their dependencies
- Course of Reminiscence: Could uncover hidden execution or delicate information
Open Recordsdata:
- Accessed Recordsdata: Sheds gentle on consumer actions
- Deleted Recordsdata: Potential proof restoration level
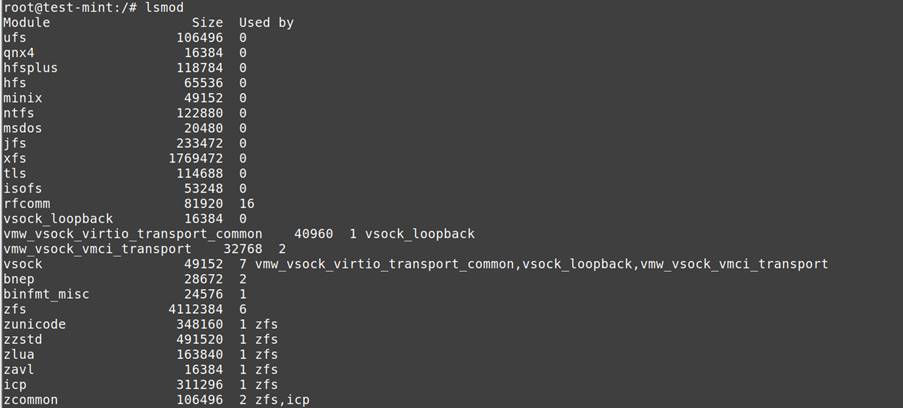
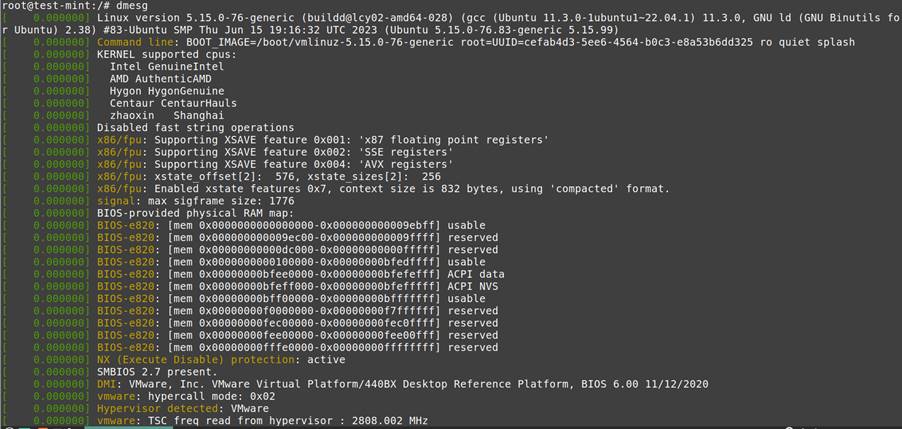
Kernel Insights
- Loaded Modules: Core extensions and potential rootkits
- Kernel Ring Buffers (dmesg): Reveals driver or {hardware} occasions
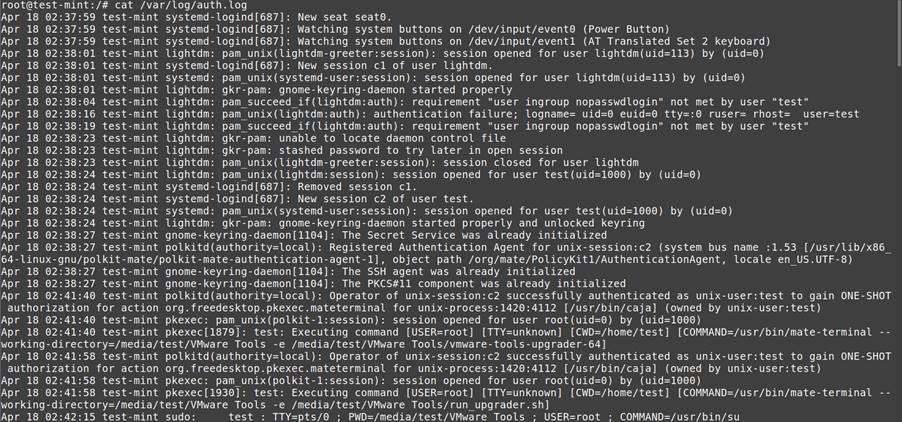
Person Traces
- Login Historical past: Person exercise monitoring
- Command Historical past: Executed instructions present insights
Earlier than diving into the acquisition course of, it is important to equip your self with the required instruments and instructions for gathering unstable information successfully, for objective of demonstration I shall be utilizing Linux Mint:
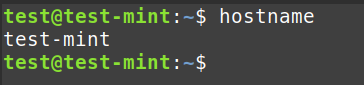
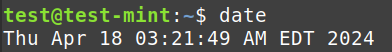
Hostname, Date, and Time:
hostname: Retrieves the system’s hostname.
date: Shows the present date and time.
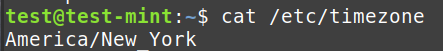
cat /and so forth/timezone:
Exhibits the system’s timezone configuration.
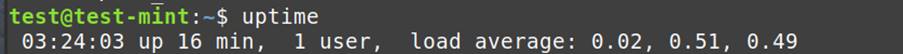
System Uptime:
uptime: Offers info on system uptime because the final restart.
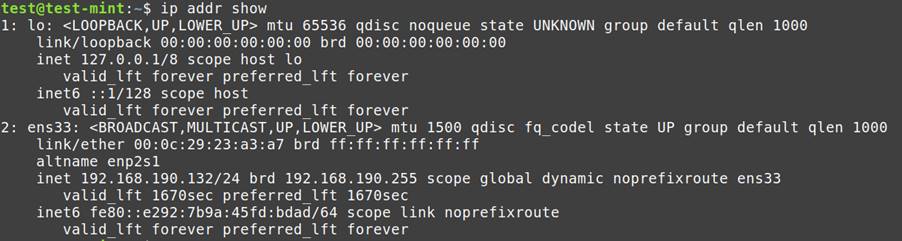
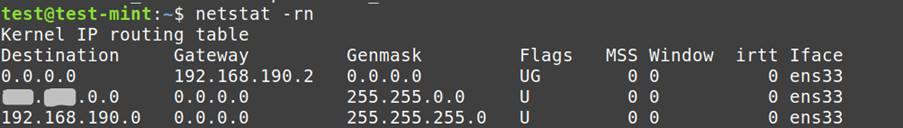
Community Footprint:
ip addr present: Lists energetic community interfaces and their configurations.
netstat -rn: Shows routing tables, aiding in understanding community connections.
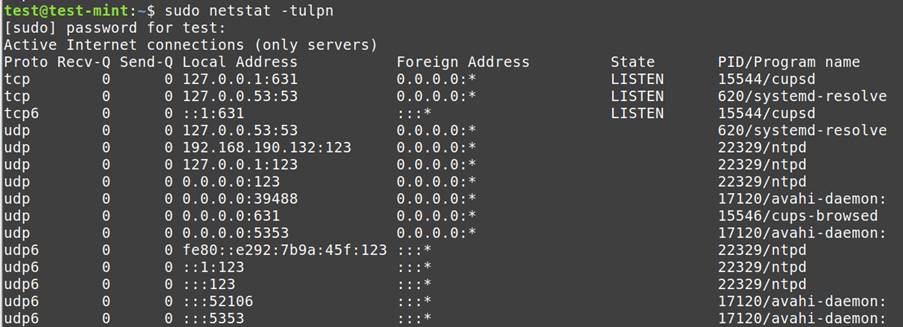
Open Ports and Lively Connections:
netstat -tulpn: Lists open TCP and UDP ports together with related processes.
lsof -i -P -n | grep LISTEN: Identifies processes listening on open ports.
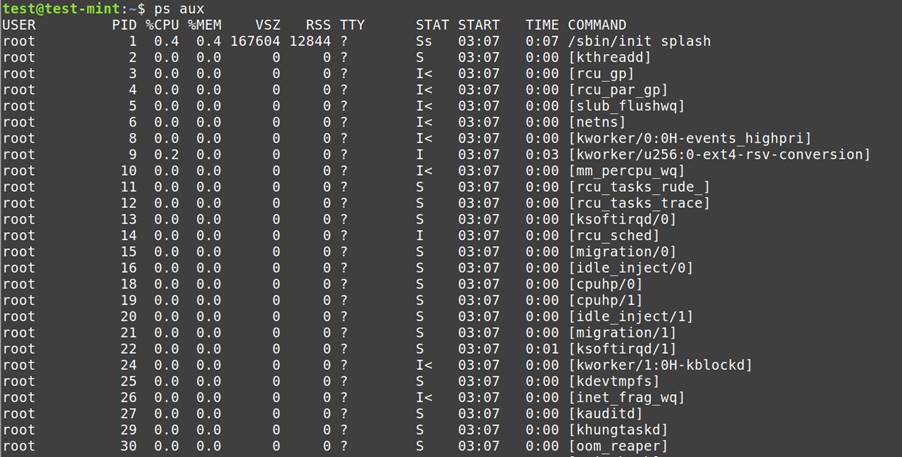
Operating Processes and Reminiscence:
ps aux: Lists all operating processes, together with their particulars.
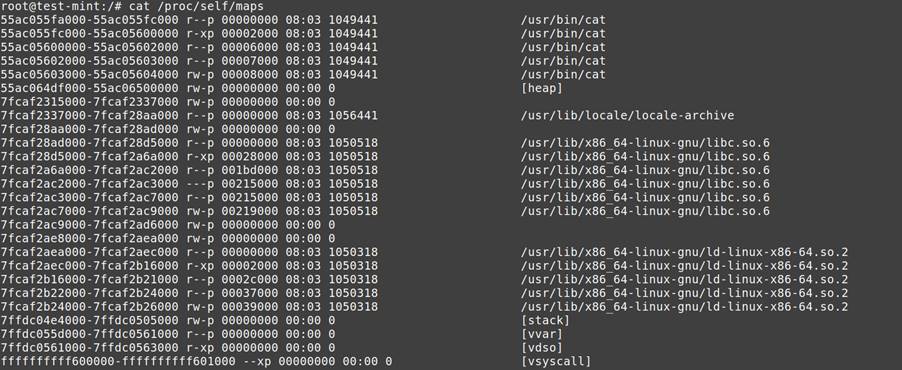
/proc/