Unknown teams have launched probes towards a zero-day vulnerability recognized in Apache’s OfBiz enterprise useful resource planning (ERP) framework — an more and more common technique of analyzing patches for tactics to bypass software program fixes.
The 0-day vulnerability (CVE-2023-51467) in Apache OFBiz, disclosed on Dec. 26, permits an attacker to entry delicate data and remotely execute code towards purposes utilizing the ERP framework, in line with an evaluation by cybersecurity agency SonicWall. The Apache Software program Basis had initially launched a patch for a associated challenge, CVE-2023-49070, however the repair failed to guard towards different variations of the assault.
The incident highlights attackers’ technique of scrutinizing any patches launched for high-value vulnerabilities — efforts which frequently end in discovering methods round software program fixes, says Douglas McKee, govt director of risk analysis at SonicWall.
“As soon as somebody’s performed the arduous work of claiming, ‘Oh, a vulnerability exists right here,’ now a complete bunch of researchers or risk actors can take a look at that one slim spot, and you’ve got form of opened your self as much as much more scrutiny,” he says. “You’ve got drawn consideration to that space of code, and in case your patch is not rock strong or one thing was missed, it is extra more likely to be discovered since you’ve further eyes on it.”
SonicWall researcher Hasib Vhora analyzed the Dec. 5 patch and found extra methods to use the difficulty, which the corporate reported to the Apache Software program Basis on Dec. 14.
“We have been intrigued by the chosen mitigation when analyzing the patch for CVE-2023-49070 and suspected the true authentication bypass would nonetheless be current for the reason that patch merely eliminated the XML RPC code from the appliance,” Vhora said in an evaluation of the difficulty. “In consequence, we determined to dig into the code to determine the basis reason for the auth-bypass challenge.”
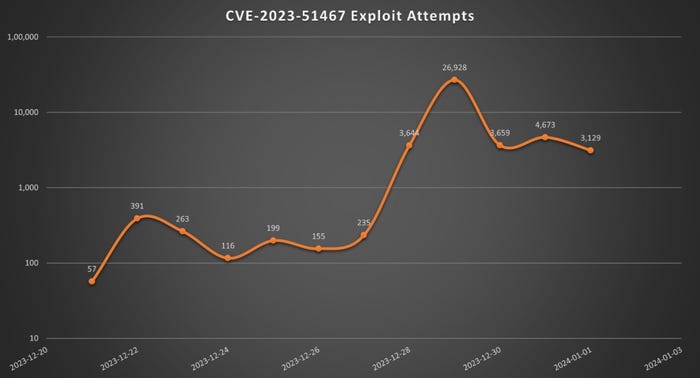
Assaults focused the Apache OfBiz vulnerability previous to its Dec. 26 disclosure. Supply: Sonicwall
By Dec. 21, 5 days earlier than the difficulty was made public, SonicWall had already recognized exploitation makes an attempt for the difficulty.
Patch Imperfect
Apache is just not alone in releasing a patch that attackers have managed to bypass. In 2020, six out of the 24 vulnerabilities (25%) attacked utilizing zero-day exploits have been variations on beforehand patched safety points, in line with knowledge launched by Google’s Menace Evaluation Group (TAG). By 2022, 17 of the 41 vulnerabilities attacked by zero-day exploits (41%) have been variants on beforehand patched points, Google said in an up to date evaluation.
The explanations that firms fail to totally patch a problem are quite a few, from not understanding the basis reason for the issue to coping with enormous backlogs of software program vulnerabilities to prioritizing a right away patch over a complete repair, says Jared Semrau, a senior supervisor with Google Mandiant’s vulnerability and exploitation group.
“There isn’t any easy, single reply as to why this occurs,” he says. “There are a number of components that may contribute to [an incomplete patch], however [SonicWall researchers] are completely proper — loads of instances firms are simply patching the identified assault vector.”
Google expects that the share of zero-day exploits that focus on incompletely patched vulnerabilities to stay a big issue. From the attacker perspective, discovering vulnerabilities in an utility is troublesome as a result of researchers and risk actors need to look by means of 100,000s or hundreds of thousands of strains of code. By specializing in promising vulnerabilities that will not have been correctly patched, attackers can proceed to assault a identified weak level moderately than begin from scratch.
A Manner Round OfBiz Repair
In some ways, that is what occurred with the Apache OfBiz vulnerability. The unique report described two issues: an RCE flaw that required entry to the XML-RPC interface (CVE-2023-49070) and an authentication bypass downside that supplied untrusted attackers with this entry. The Apache Software program Basis believed that eradicating the XML-RPC endpoint would stop each points from being exploited, the ASF safety response group stated a response to questions from Darkish Studying.
“Sadly we missed that the identical authentication bypass additionally affected different endpoints, not simply the XML-RPC one,” the group stated. “As soon as we have been made conscious, the second patch was issued inside hours.”
The vulnerability, tracked by Apache as OFBIZ-12873, “permits attackers to bypass authentication to realize a easy Server-Aspect Request Forgery (SSRF),” Deepak Dixit, a member on the Apache Software program Basis, said on the Openwall mailing checklist. He credited SonicWall risk researcher Hasib Vhora and two different researchers — Gao Tian and L0ne1y — with discovering the difficulty.
As a result of OfBiz is a framework, and thus a part of the software program provide chain, the impression of the vulnerability could possibly be widespread. The favored Atlassian Jira challenge and issue-tracking software program, for instance, makes use of the OfBiz library, however whether or not the exploit might efficiently execute on the platform continues to be unknown, says Sonicwall’s McKee.
“It’ll rely upon the best way every firm architects their community, in the best way they configure the software program,” he says. “I’d say a typical infrastructure wouldn’t have this Web-facing, that it could require some sort of VPN or inside entry.”
In any occasion, firms ought to take steps and patch any purposes identified to make use of OfBiz to the newest model, the ASF safety response group stated.
“Our advice for firms that use Apache OFBiz is to comply with safety greatest practices, together with solely giving entry to programs to these customers that want it, ensuring to frequently replace your software program, and ensuring you might be well-equipped to reply when a safety advisory is printed,” they stated.
